solution
Protect important corporate data and fight against encrypted ransomware
Date:2019-05-20 Views:28205
Protect important corporate data and fight against encrypted ransomware
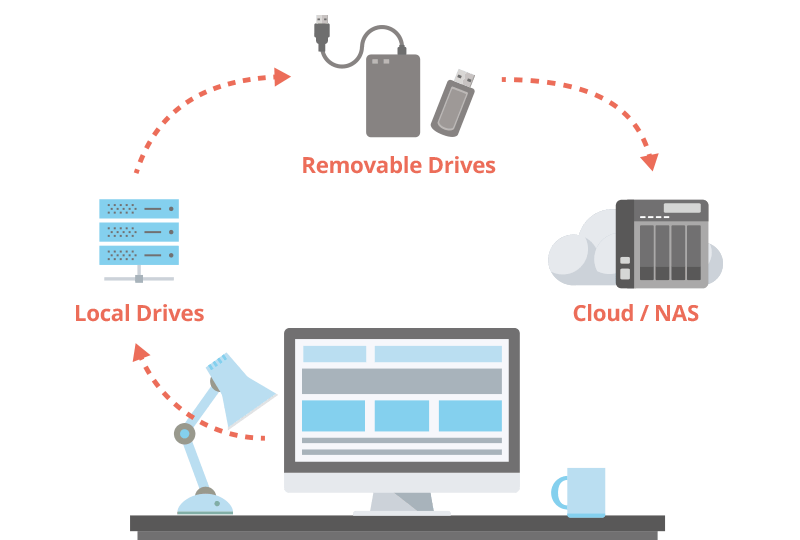
Small and medium-sized enterprises can defend against the threat of encrypted ransomware through network storage service solutions (NAS + security strategy + backup).
Encrypted ransomware (Ransomware) attacks on computers and network equipment are increasing and difficult to prevent. No matter whether it is an enterprise organization or a home user, it cannot be taken lightly. To counter the threat of ransomware, you need a simple and effective method to ensure that you always have the latest backup files. The network storage (NAS) solution provides a perfect backup function and snapshot mechanism, which effectively helps individuals or organizations protect important data, restore files, and avoid work or service interruption. It is a good file backup solution.
What is encrypted ransomware?
Global malicious ransomware computer viruses, such as Cryptolocker, CTB Locker and TeslaCrypt, encrypt files stored in computers, mobile hard drives, mounted network drives (Mapped Network Drive), and even Dropbox sync folders. Once infected, the victim will be required to pay a ransom within the stipulated period to decrypt these files, otherwise they will be unable to open these maliciously encrypted files and lose precious data.
Why are these encrypted ransomware viruses so tricky?
●Most encrypted ransomware is not only disguised as .exe files in .zip, .pdf, .doc, .exe, .js and other file types through phishing email attachments, but also more likely to be directly hidden in the website, which is not only difficult Identify, copy and spread by myself.
●Encrypted ransomware is continuously updated, making it impossible for general antivirus software to detect it in real time.
●Encrypted ransomware may use Asymmetric Encryption or other technologies in the process of data encryption, making local encryption difficult to crack.
●The victim will be ransomed to pay the ransom (through the anonymous network and Bitcoin that are difficult to track) to restore access, otherwise the encrypted file will never be opened.
Use network storage (NAS) solution> Backup files to protect precious data
The first line of defense against malicious virus attacks is to maintain vigilance and prudence in network usage habits at all times, such as: regularly updating system software, not opening suspicious emails, not downloading unknown files, not visiting unknown websites, etc. Many antivirus experts It is unanimously believed that backing up data at any time is the most basic and important method of data preservation. "Qinjia backup" is the only way.
Network storage (NAS) solutions provide simple solutions to help you back up and restore files and data. It uses a Linux-based operating system, which is more secure and reliable than the vulnerable Windows system. In addition, the advanced block-level snapshot function (Block-based Snapshot) of the file system makes network storage (NAS) a reliable data backup solution. Even if the file system has been encrypted by a virus, you can still use snapshots to restore important data in real time. Files and system data.
Snapshot: Quickly backup and restore data
The snapshot of the network storage (NAS) solution can record the system state and data (including metadata) at any point in time and be separated from the file system. Even if the files in the NAS have been infected with encrypted ransomware, the snapshot will not be affected. Users can quickly save files, folders, or even entire volumes at different points in time through snapshots, and restore them at any time. If your system is infected with encryption ransomware or accidental damage occurs, snapshots can help your system quickly restore to its original normal state. It is recommended that you store the files on the NAS or add more backups to ensure data security.

Block-level snapshot

one click recovery
It only takes a few minutes to restore files using snapshots. Since the snapshot is separated from the file system, even if the files in the disk area are infected by the ransomware, the snapshot data can still be selected in real time and restored.
Snapshot synchronization(Snapshot Replica)
After the snapshots are created, you can back up these snapshots to a remote NAS or server again to ensure double protection.

Snapshot reserve space
If the encrypted ransomware continues to write data, it may cause insufficient storage space, making the snapshot protection unable to function properly. Its "Snapshot Reserve Space" function can reserve specific storage space for snapshots by default, avoiding the above problems.
For specific usage details, pleasecontact us。
- Next:Excellent file









